Lab 2d: Prevent uploads to non-corporate cloud services
Estimated Time: 10 minutes
OVERVIEW
Modern enterprise companies typically want users to benefit from cloud services, e.g. having better collaboration, working more efficiently and achieving faster time to market. Therefore, users can often use cloud storage applications, which comply with companies "enterprise-readiness" criteria.
However, it is essential that companies' intellectual properties remain inside companies' own or IT-controlled environment. One relatively easy way to achieve this is to prevent uploads to unmanaged cloud storage apps and instances. This is achieved with three (3) policies:
-
Coach users that upload files to cloud storage to differentiate between company and private content (this lab, Lab 2d)
-
Allow corporate cloud storage (next lab, Lab 2e)
-
Ensure that company confidential files stay "inside" (Lab 2f)
Step 1 Using your web browser, go to this awesome Shadow-IT cloud storage named WeTransfer: [https://wetransfer.com]
Because it is often used by 3rd party or partners to workaround size limitations in email, you cannot really block it without creating business or user friction.
Thus, login, browsing and download should be ok.
Step 2 However, try to upload any file from your computer and you should get coached not to do so.
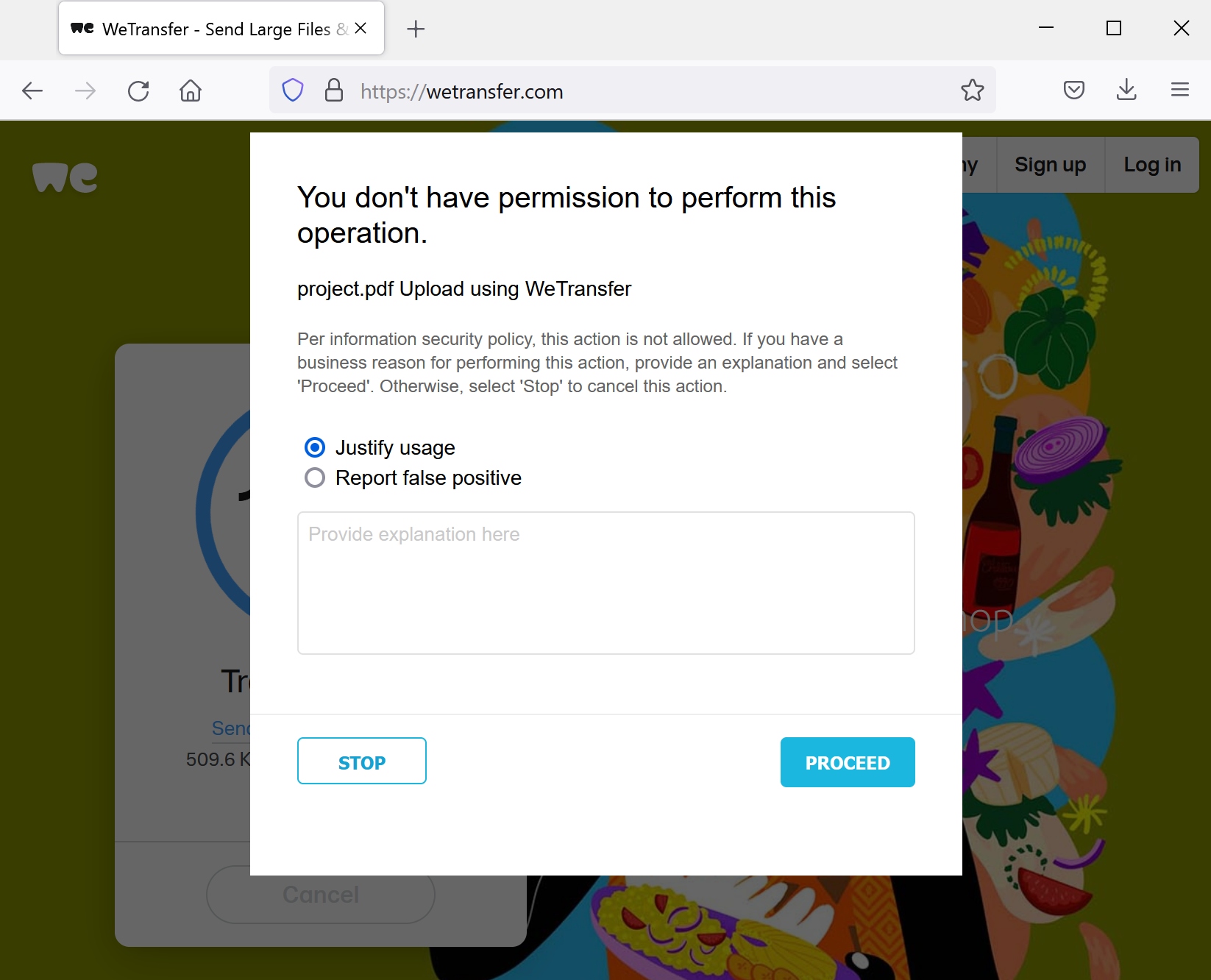
These kinds of user notifications train the individuals in companies and greatly reduce the amount of helpdesk calls.
Remember, the files which we have a look at in this scenario, are either private or normal company files. Corporate confidential files will be handled differentially and covered in the next lab.
Step 3 In your Netskope tenant, navigate to SkopeIT > Application
Events and select "Last 24 hours". There should be several entries
listed. If needed, click the
 query mode icon and enter the query app
eq 'WeTransfer' and user eq 'emea.csw[X]@yopmail.com' in the
search field and enter. Replace [X] with your pod number.
query mode icon and enter the query app
eq 'WeTransfer' and user eq 'emea.csw[X]@yopmail.com' in the
search field and enter. Replace [X] with your pod number.
Step 4 Look for a WeTransfer entry for your user regarding your activity. Expand by using the spyglass icon to see what details are available. Find out which policy triggered here and have a closer look at what is configured in that policy.
AGAIN, please do not change it.
NOTE You should find a single policy ; applicable to hundreds of cloud storage apps.
Some NGFW or UTM vendors claim they can do Application Control instead. Think about the number of policy you would have to write. Netskope policies are way more efficient.
In addition, competitors usually cannot handle cloud-to-cloud

Please continue onto the next section.