Lab 2e: Allow usage (incl. uploads) of [corporate] O365 instance
Estimated Time: 15 minutes
OVERVIEW
In this lab, you will explore how to allow sanctioned instances of applications that are being used on your network. You will also provide security coaching to users who are attempting to perform risky activities. You can use these steps on your own network to prevent users from engaging in risky behaviors in the cloud. You will also draw up reports for analysis of activity in the network.
Applicable Use Cases
-
Identify and grant access to specific (corporate) application instance
-
Block risky activities
Prerequisites
-
Access and credentials to the Netskope tenant ([https://csw2-emea.eu.goskope.com/])
-
Use the same admin credentials like before.
-
Netskope Steering Client installed (requires local admin rights)
WALKTHROUGH
In this lab you act as an administrator allowing only access to a corporate sanctioned version of the collaboration application Microsoft / Office 365 (including OneDrive). You will first identify that all uploads to your corporate O365 OneDrive is working with the user alert we saw in Lab 2. Then you create a policy on the Netskope Security Cloud to allow uploads for your user to only the NetskopeCSW instance of Microsoft / Office 365.
Our corporate Microsoft / Office 365 tenant for this lab: no longer valid.onmicrosoft.com
Step 1 Verify first that you can not upload files to your corporate OneDrive. Navigate to [https://www.office.com] and click Sign in, located at the left of the page.
Alternatively, you can also use this link which is public Sharepoint folder from a malicious actor: [https://453kv8-my.sharepoint.com/:f:/g/personal/neo_453kv8_onmicrosoft_com/EkW0PgxT9ANMqcV5Yd8OgkkBLHO47t8TcjI4LhoRx7lBaA]
Step 2 Enter your individual corporate Microsoft / Office 365 or a user login that you received in your workshop preparation email:
login: no longer valid.onmicrosoft.com
Pa$$w0rd: no longer valid
Step 3 Open OneDrive...
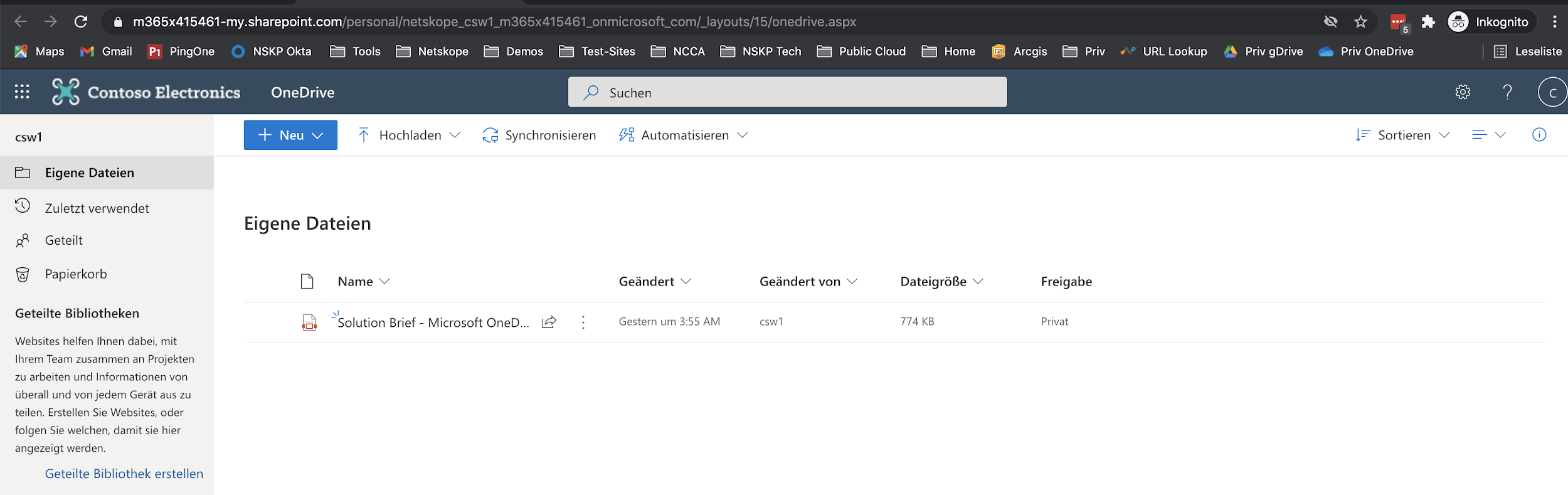
Step 4 Now, please try to upload any file from your local computer. You should receive a coaching user notification to explain that it is not allowed to upload company files to non-corporate cloud storage applications. If other than the corporate use of that upload (e.g. private files), it might be ok to do so (like in the lab before).
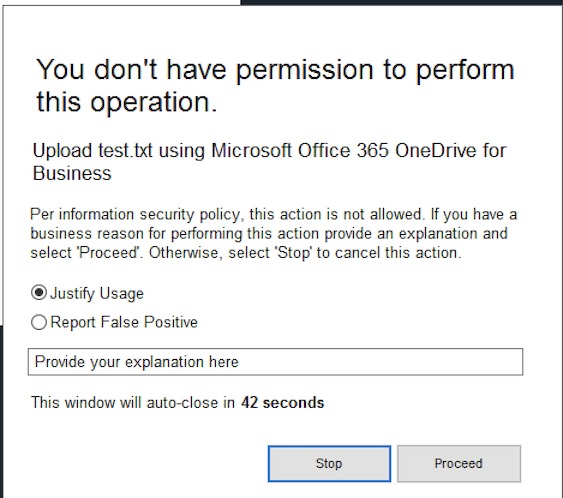
Step 5 Goal now is to allow all file uploads without coaching user notifications for the corporate OneDrive instance.
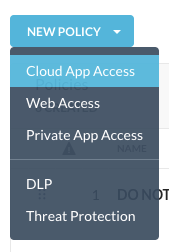
From the home screen of your Netskope tenant, Navigate to Policies > Real-time Protection, click new policy, "Cloud App Access".
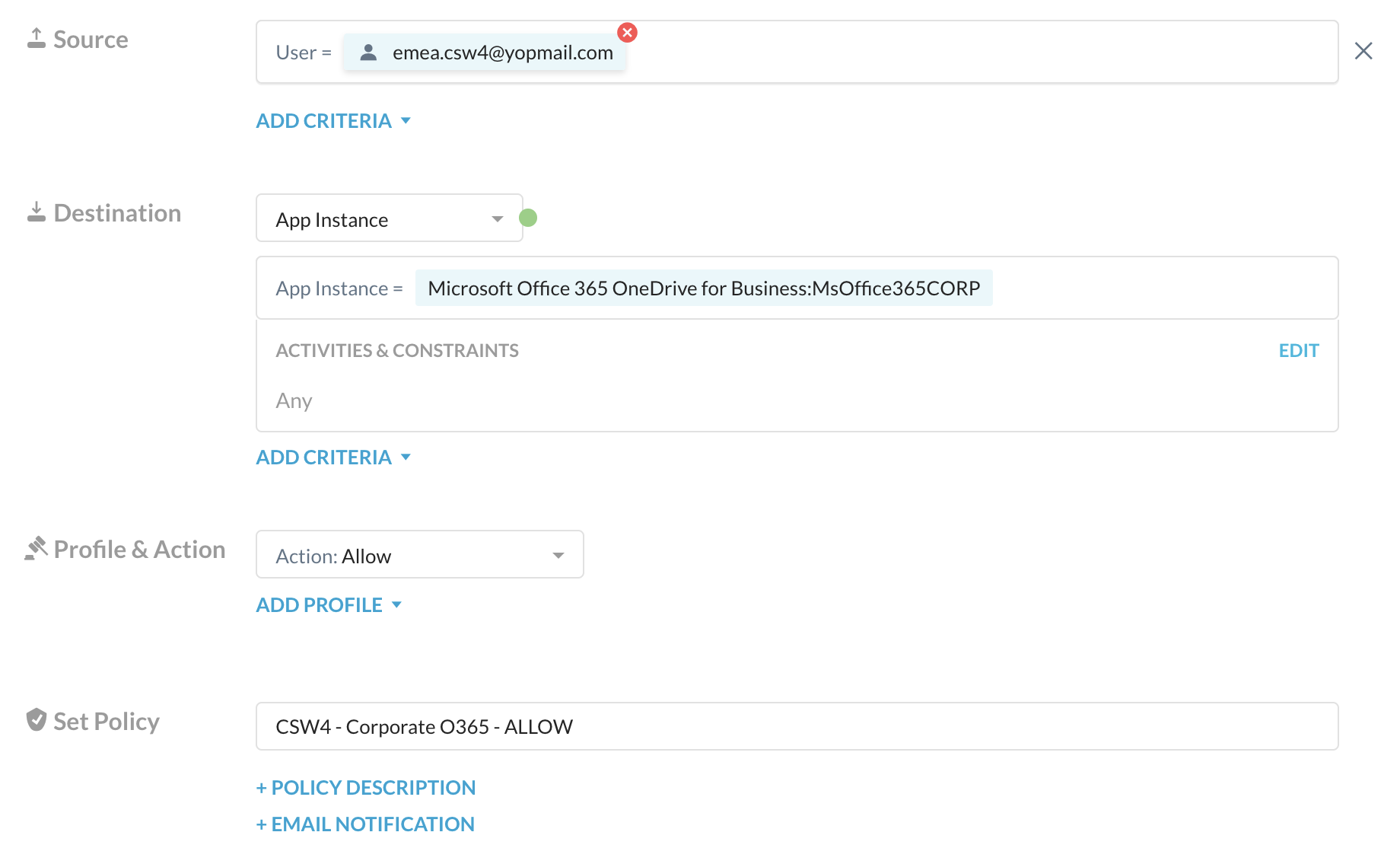
Step 6 Select:
- your username in the users section,
- Destination: select the App Instance from the drop-down menu
- then "Microsoft Office 365 OneDrive for Business: MsOffice365CORP" from the list
- Action: select Allow
- Set Policy name: CSW[X] - Corporate O365 - Allow
It should look like this:
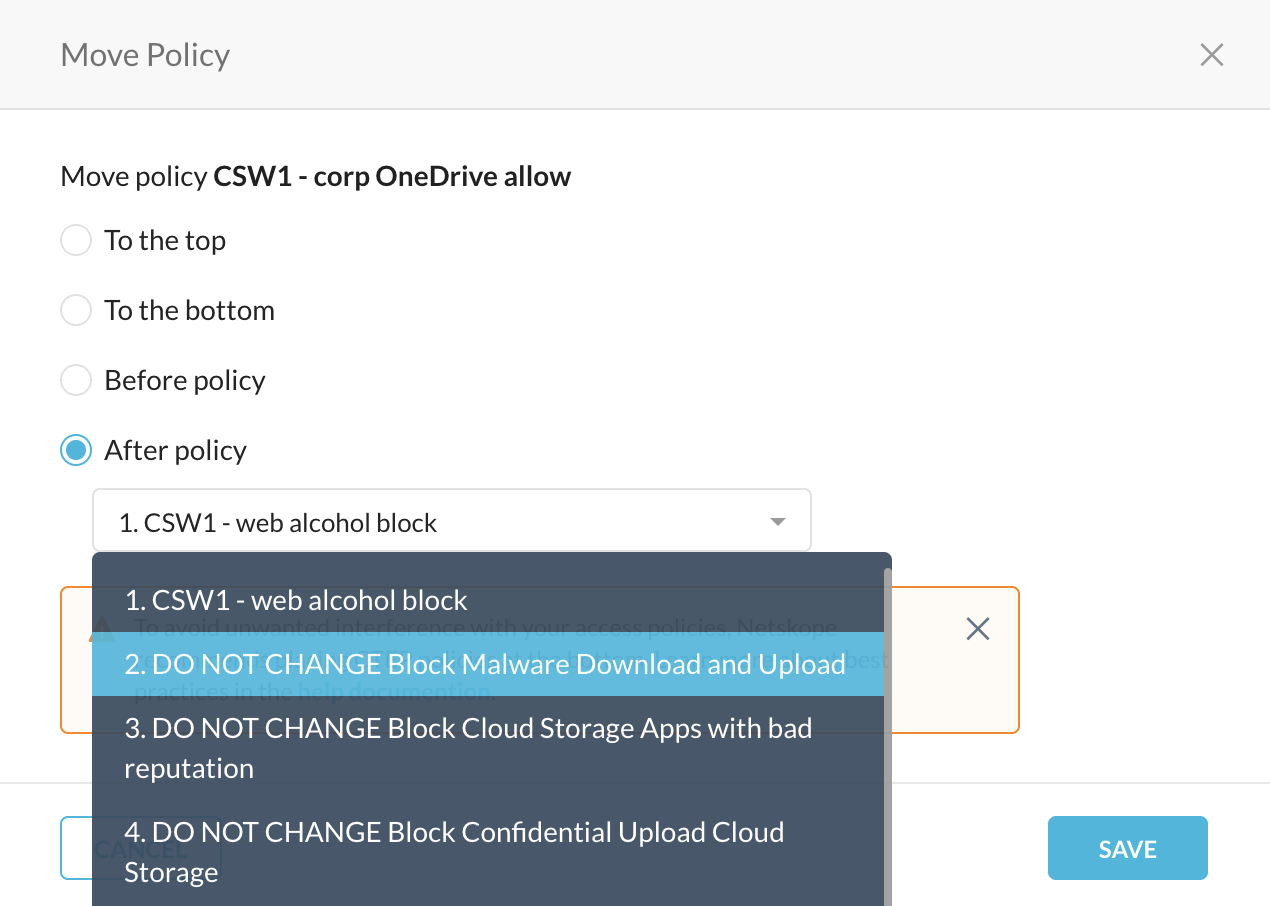
Step 6 Click Save and select After policy "DO NOT CHANGE Block Malware Download and Upload".
Step 7 Don't forget to apply changes (and wait about 30 seconds).
Step 8 Now, go back to your corporate OneDrive and try to upload a file again. That should work now without user coaching, as you upload files to the corporate cloud storage.
Step 10 What about other OneDrive instances (one from an attacker for example) ?
File upload to any other instance (from private/personal to contractors, partners, or other unmanaged subsidiaries) should not be allowed directly BUT should be coached.
Go back AGAIN to [https://portal.office.com] (use a new incognito / private browser window) and login with a "shadow-it" Microsoft / Office 365 account:
login: no longer valid.onmicrosoft.com
Pa$$w0rd: no longer valid
Step 11 Login works fine, and if you try to upload files, you still receive the coaching user notification - like in Lab 2d.
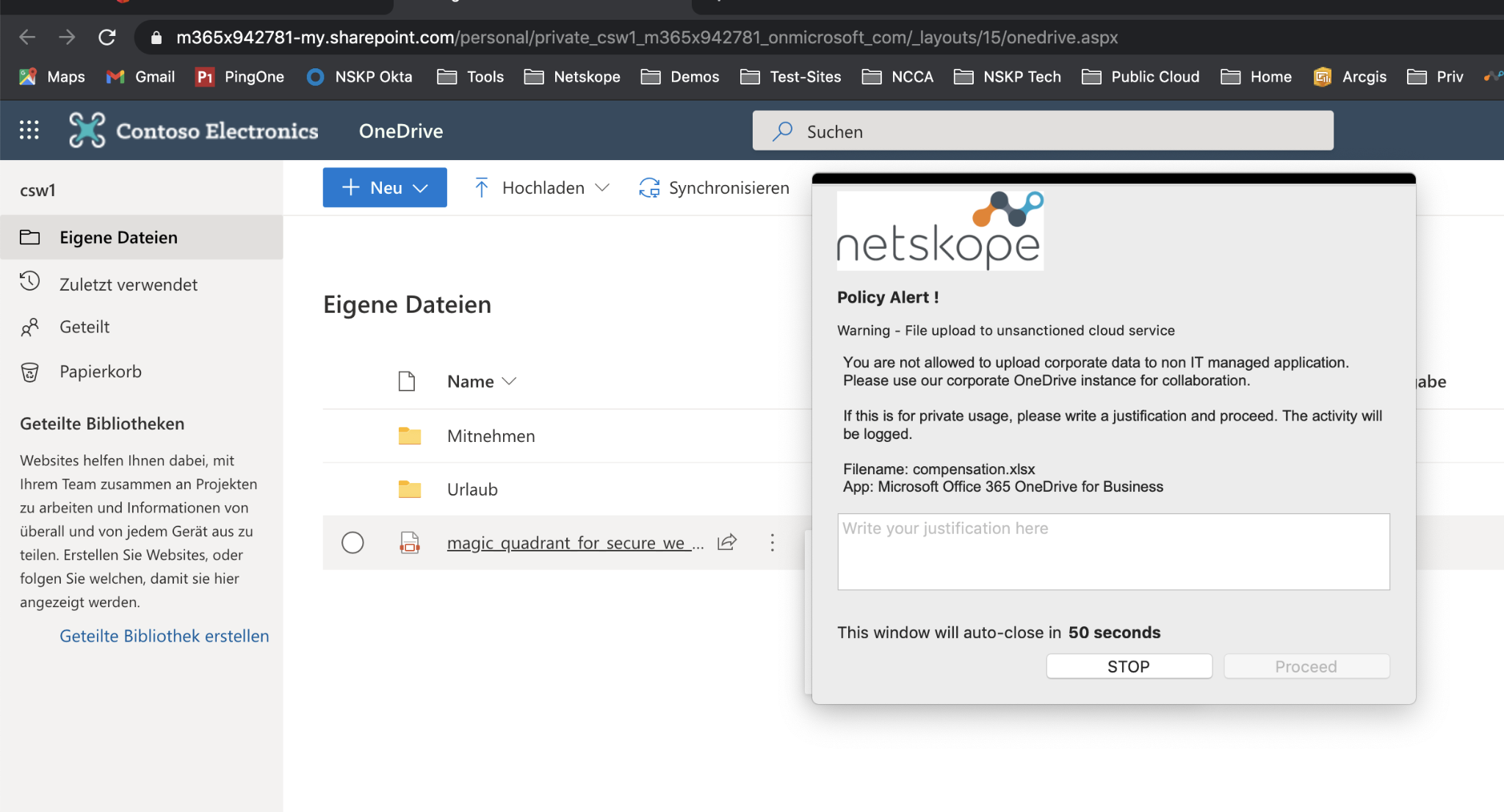
That's OK, but it could be improved as we don't want people to click "proceed anyway" and sensitive files to be uploaded to this place.
This will be solved in the next lab.

Please continue onto the next section.